Identify threats, prioritize investment, and communicate cyber risk to stakeholders.


See exposure across your entire attack surface.
Cyber risk management
Our solutions.
Identify exposure, prioritize investment, communicate with stakeholders, and mitigate risk to protect your expanding digital ecosystem. The only provider that cuts across the first, third, and fourth party risk to identify what is truly putting your organization in harm's way.
Why Bitsight?
Day one impact. That’s the difference.
The largest risk dataset anywhere.

The largest risk dataset anywhere.
Know what you’re up against with cyber risk data that maps your entire ecosystem. Processing over 400 billion events daily. Rating 40 million companies. Precisely pinpointing your risk. At speed, and at scale.
Speak the universal language of cyber risk management.

Speak the universal language of cyber risk management.
To gain alignment, you’ve got to get everyone on the same page. As the only independently verified rating with clear correlation to critical outcomes, we’re the go-to for market leaders who want buy-in from their board.
Cyber risk is business risk. And we speak business.

Cyber risk is business risk. And we speak business.
We go beyond cyber risk ratings to provide actionable financial and business insights. Because if you want to improve your performance or sway the board to invest, you need to speak their language.



Use Cases
Clarity for cyber leaders.
Continuous monitoring
Key benefits
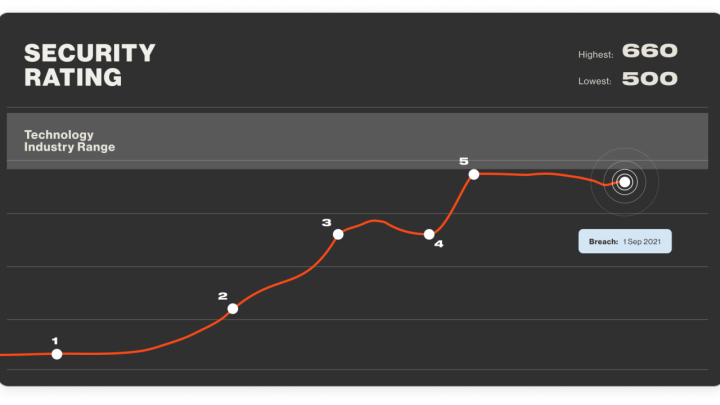
Continuous monitoring
Key benefits
- Find hidden risk in third and fourth parties
- Remediate with in-context collaboration
- Access reports that translate cyber risk into business risk
Vendor risk management
Key benefits
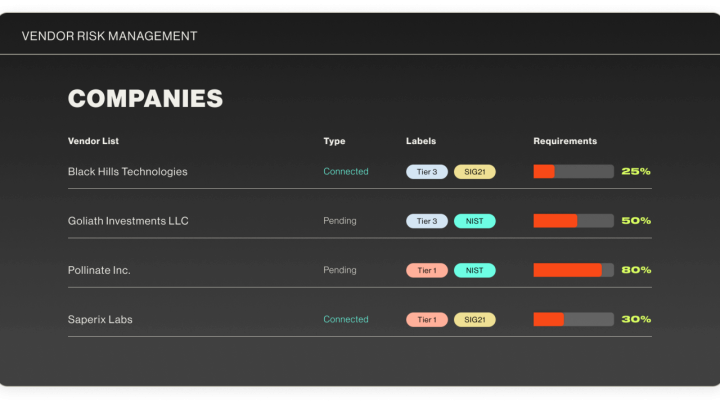
Vendor risk management
Key benefits
- Accelerate risk assessments with a 20,000 vendor network
- Validate questionnaires with objective data
- Gain intelligence through integrated data feeds
Exposure management
Key benefits
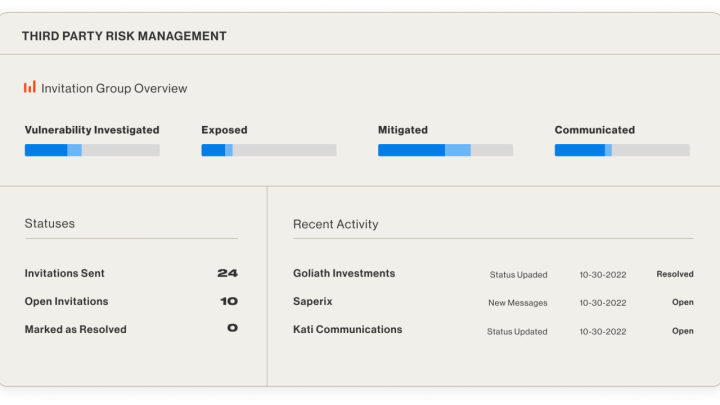
Exposure management
Key benefits
- Detect & respond to major security events in your digital ecosystem—with speed
- Track vendor response to exposure in real time
- See the whole view of your attack surface—continuously
- Prioritize vulnerable areas to protect your business
Cyber risk governance
Key benefits
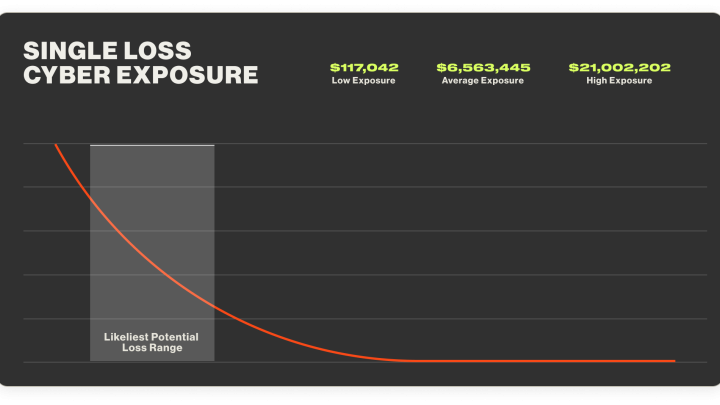
Cyber risk governance
Key benefits
- Drive accountability across your organization
- Understand progress over time with meaningful metrics
- Measure your financial exposure to cyber risk
Board-level reporting
Key benefits
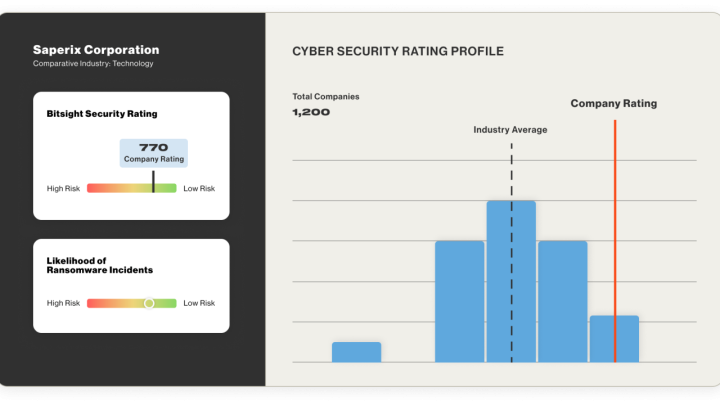
Board-level reporting
Key benefits
- Prove your program performance to the board
- Translate cyber risk into financial risk
- Give meaningful context to your metrics
Customer Success Stories
When others are cautionary, be the visionary.


Bitsight has allowed us to automate our security monitoring process, resulting in about 50 percent time and efficiency savings. We can sign into Bitsight and get real-time information right from the easy-to-use dashboard.


Our vision is to foster trust in the value chain. That is only possible with robust cyber conversations with our partner ecosystem. That is the reason why we use Bitsight technology and advisory capabilities, among other means, as part of those conversations.


With the data-driven insights that Bitsight provides, we can communicate our commitment to security excellence to insurers over time and relative to others in our space. Our risk appetite is also better understood, making it easier to negotiate the type of risk we are willing to accept, mitigate, or transfer.
Eyes on the industry
Cyber risk resources

Reports and Research
Bitsight & Google Collaborate to Analyze Cybersecurity Controls of 100k Global Organizations
Reports and Research
The Marsh McLennan Cyber Risk Analytics Center Study
Reports and Research






